Defeating Windows API Hashing in Malware with Hashdb-Ghidra
When analyzing malicious Portable Executables (PE), the Import Address Table (IAT) holds significant importance from an analyst’s perspective. The IAT is a crucial component of the PE format that records the addresses of functions imported from other Dynamic Link Libraries (DLLs). Understanding the function imports allows us to assess the capabilities of the malware. Malware developers employ various obfuscation and evasion techniques to conceal the Import Address Table. One such technique is API hashing, where the actual function names are replaced with hash values. By employing API hashing, malware authors attempt to hinder the detection and analysis of malicious code.
Resolving Windows API hashing calls can be a challenging task for analysts. One approach to tackle this issue is by dynamically executing the malware and setting breakpoints. However, this method requires significant time and in-depth analysis, making it a cumbersome process for analysts. This is where Hashdb comes into play.
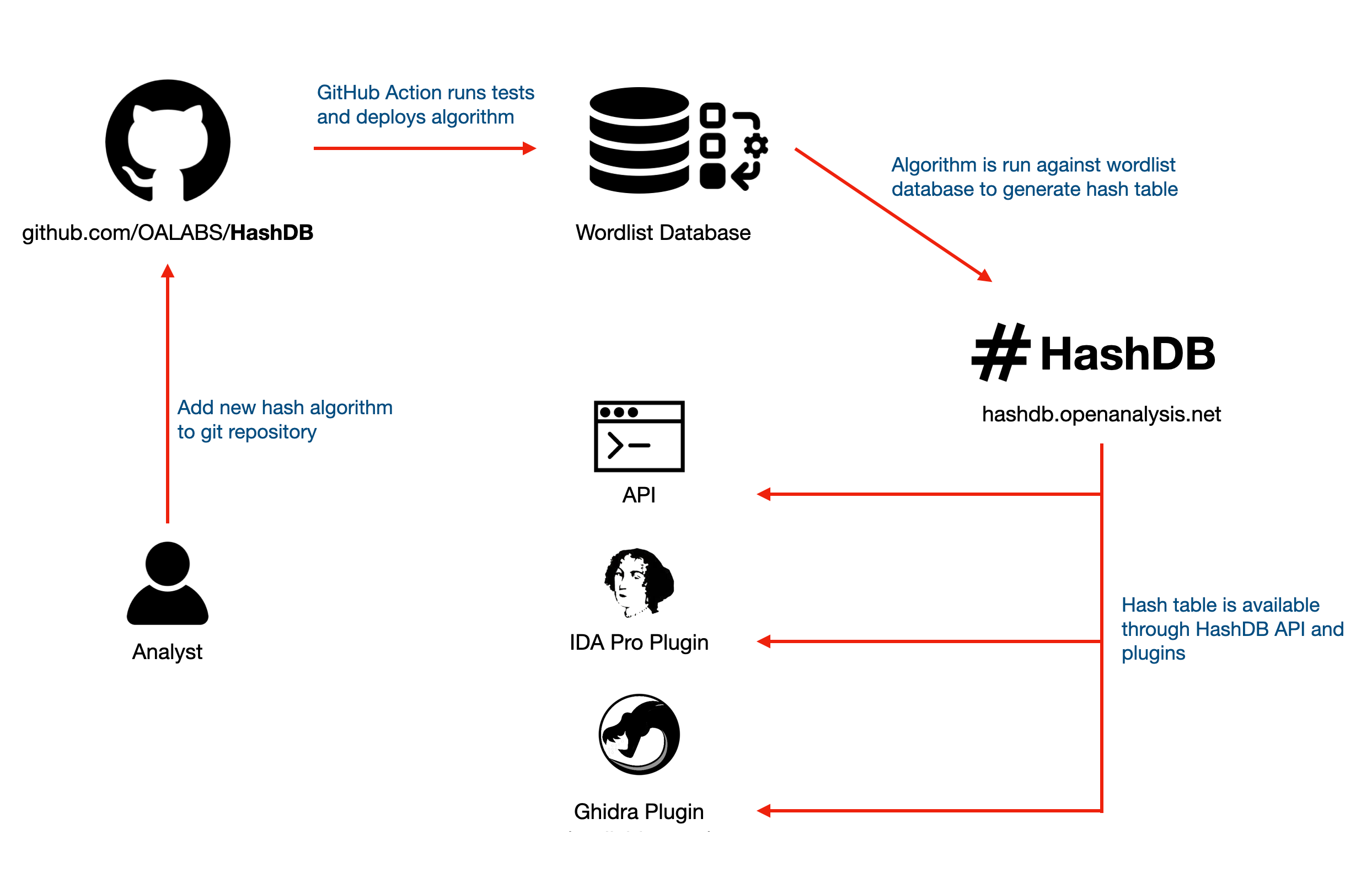
It is free community-source solution to malware API hashing thanks to OALabs. It leverages a GitHub repository as its backend, allowing analysts to contribute their own hashing algorithms. These algorithms are run against a comprehensive word list, generating a hash table. The hash table is accessible through an API or an Ghidra or IDA client.
Reflective Ransomware
49e600928f341599650c3c6d7e1bdc79 ransomware.bin
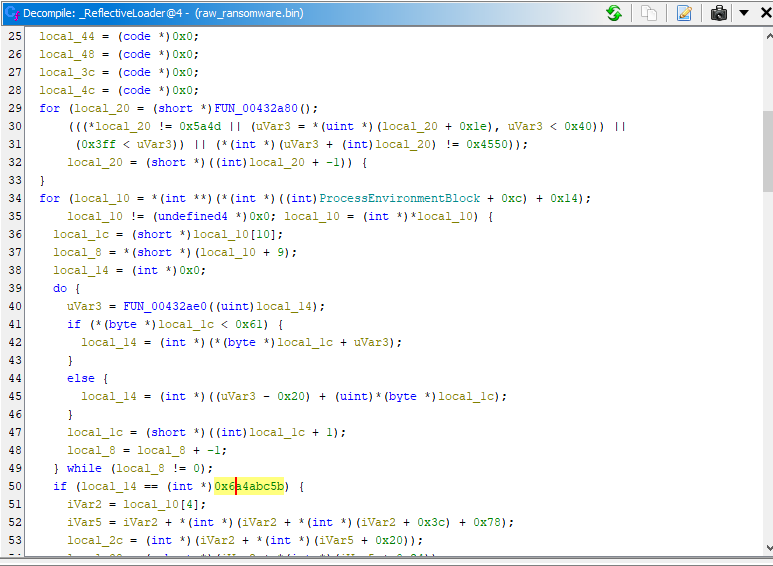 Reflective Loader subroutine uses API Hashing to resolve API related to Process injection
Reflective Loader subroutine uses API Hashing to resolve API related to Process injection
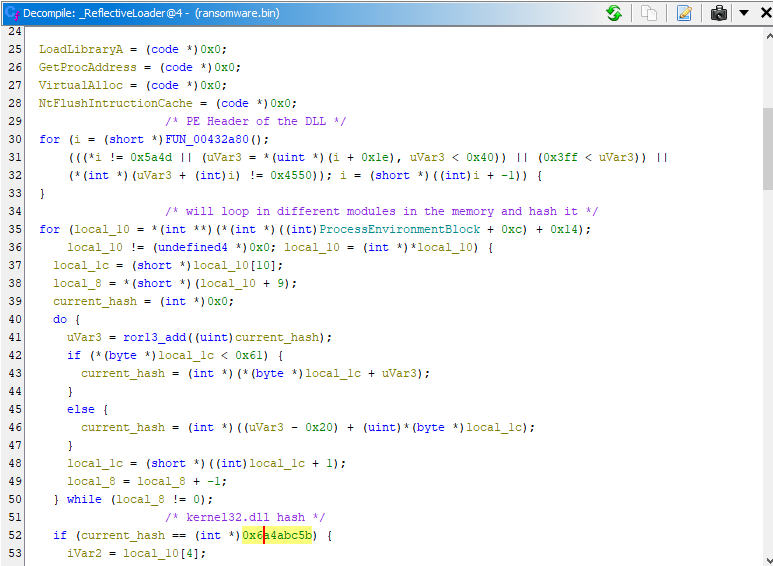 API hash resolve LoadLibraryA() GetProcAddress() VirtualAlloc() and NtFlushInstructionCache() using hashdb plugin
API hash resolve LoadLibraryA() GetProcAddress() VirtualAlloc() and NtFlushInstructionCache() using hashdb plugin
Installing Hashdb in ghidra
Ghidra latest update switch from nashorn engine (deprecated) to jython use this version db instead:
- Download hashdb-ghidra
- Copy
HashDB.javato yourghidra_scriptdirectory. - Add the location where
HashDB.javais located to your script directory search path in Ghidra’s ScriptManager.
With the latest update of Ghidra, there has been a switch from the deprecated Nashorn engine to Jython. To accommodate this change, you can use the latest pull request version:
- Download the it from here
- Copy the “HashDB.java” file to your “ghidra_scripts” directory.
- Add the location of the “HashDB.java” file to the search path in Ghidra’s ScriptManager.
By following these steps, you’ll be able to integrate and use the updated HashDB version seamlessly within Ghidra, ensuring efficient analysis of hash-related tasks.
Usage
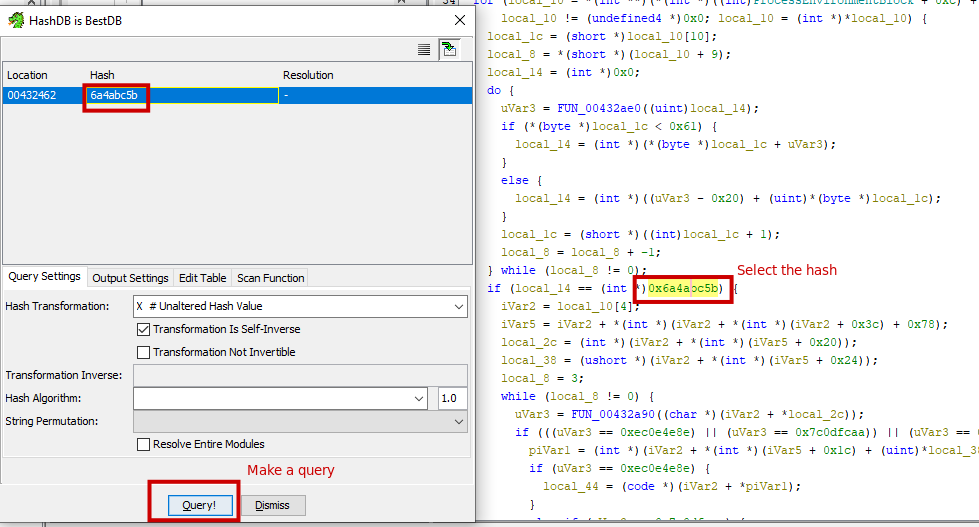
To utilize the HashDB plugin in Ghidra, follow these steps: select the hash you want to analyze, then press F3. This action triggers a popup box, prompting you to make a query in the HashDB database.
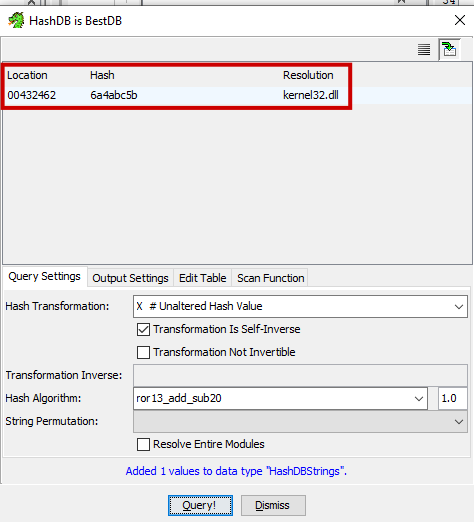
Once the query is made, the plugin will resolve the hash and display the corresponding result. For example, if the hash 0x6a4abc5b is entered, the plugin will reveal that it resolves to “kernel32.dll,” providing valuable information about the hashed item.
References
- https://www.ired.team/offensive-security/defense-evasion/windows-api-hashing-in-malware
- https://github.com/OALabs/hashdb-ghidra
- https://raw.githubusercontent.com/OALabs/hashdb-ghidra/f4c96719e05391af3ddd764f93f12cf6604472aa/HashDB.java
- https://github.com/LloydLabs/Windows-API-Hashing
- https://blag.nullteilerfrei.de/2019/11/09/api-hashing-why-and-how/