THM-Writeups Conti Ransomware
An Exchange server was compromised with ransomware. Use Splunk to investigate how the attackers compromised the server.
Task 1 SITREP
1.0 Start the attached virtual machine.
Username: bellybear
Password: password!!!
Splunk URL: http://MACHINE_IP:8000
Answer: No answer needed
Task 2 Exchange Server Compromised
2.0 Can you identify the location of the ransomware?
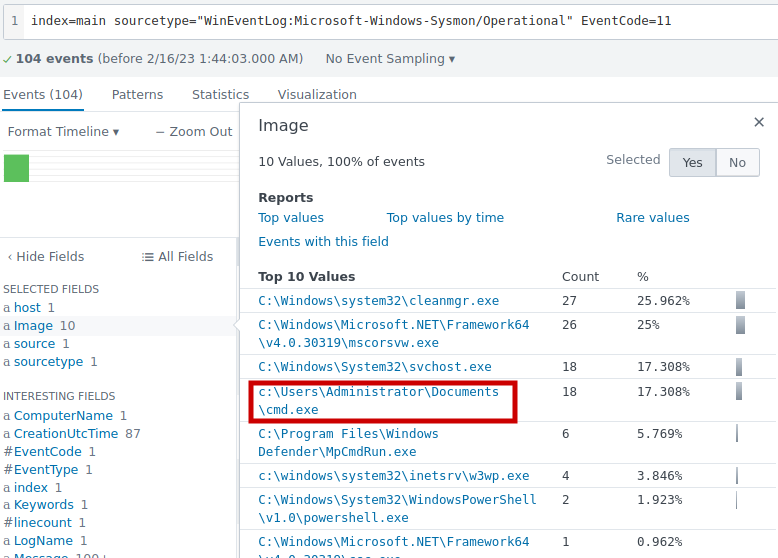
We can start to find the location of ransomware by using sysmon event ID 11.
index=main sourcetype="WinEventLog:Microsoft-Windows-Sysmon/Operational" EventCode=11
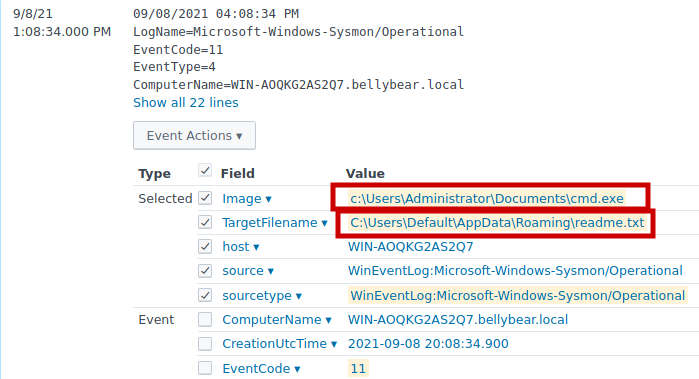
Using Sysmon event code 11 to filter the logs. We can se that there is a unusual file named cmd.exe on Document folder of the Administrator.
The file also drops a readme.txt which is the ransomware note.
Answer: c:\\Users\\Administrator\\Documents\\cmd.exe
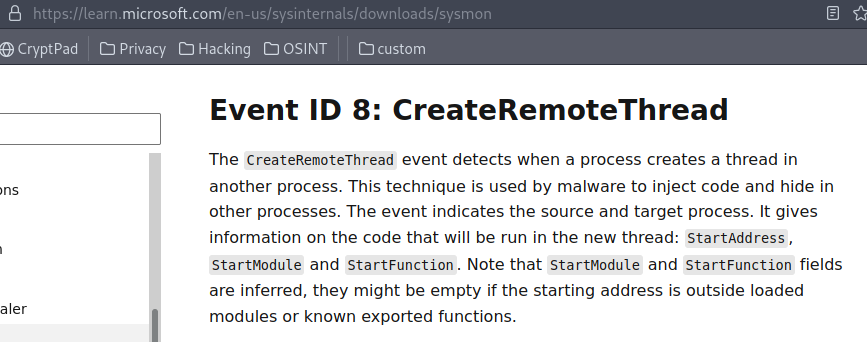
2.1 What is the Sysmon event ID for the related file creation event?
https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon
Answer: 11
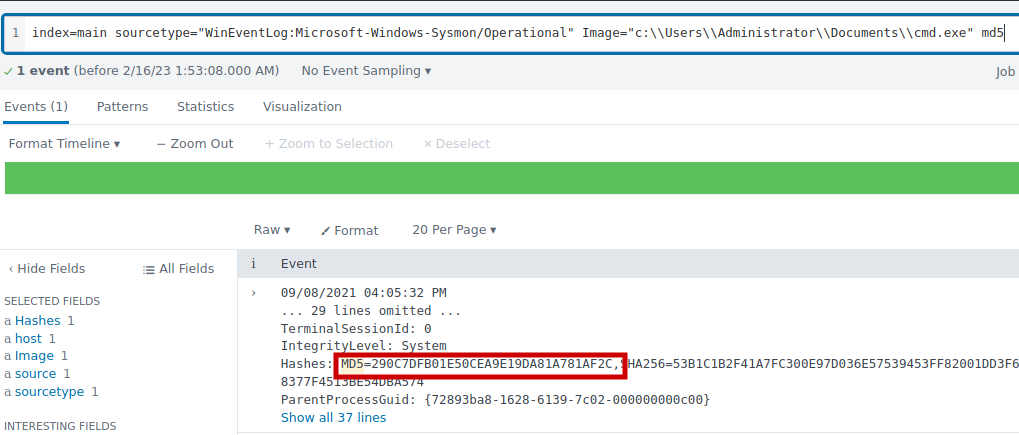
2.2 Can you find the MD5 hash of the ransomware?
index=main sourcetype="WinEventLog:Microsoft-Windows-Sysmon/Operational" Image="c:\\Users\\Administrator\\Documents\\cmd.exe" md5
Answer: 290C7DFB01E50CEA9E19DA81A781AF2C
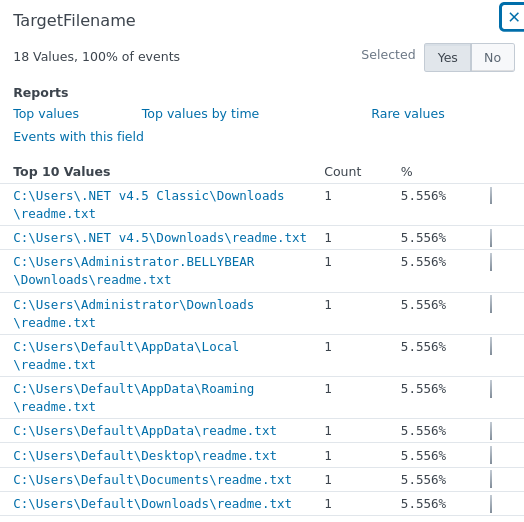
2.3 What file was saved to multiple folder locations?
index=main sourcetype="WinEventLog:Microsoft-Windows-Sysmon/Operational" EventCode=11 TargetFilename="*readme.txt"
The ransomware note, readme.txt, which is dropped by cmd.exe in the Admin Document directory, saves in multiple folder locations.
Answer: readme.txt
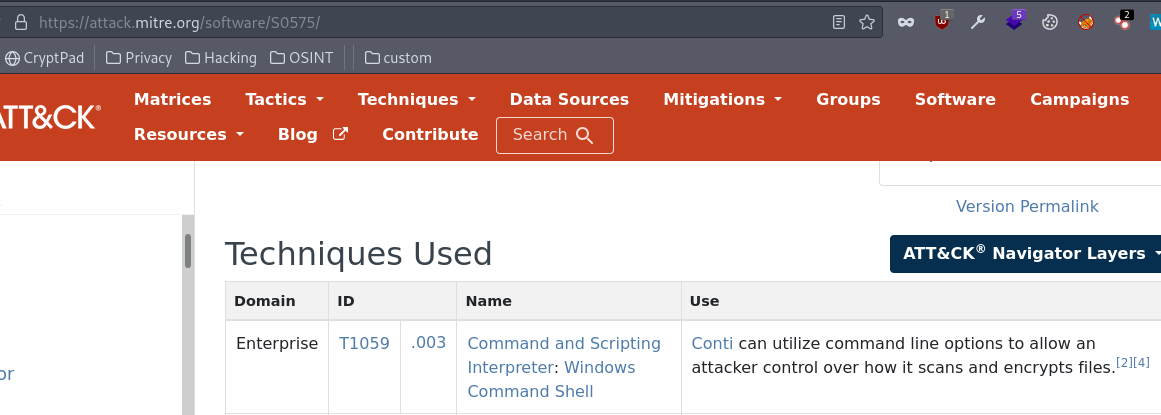
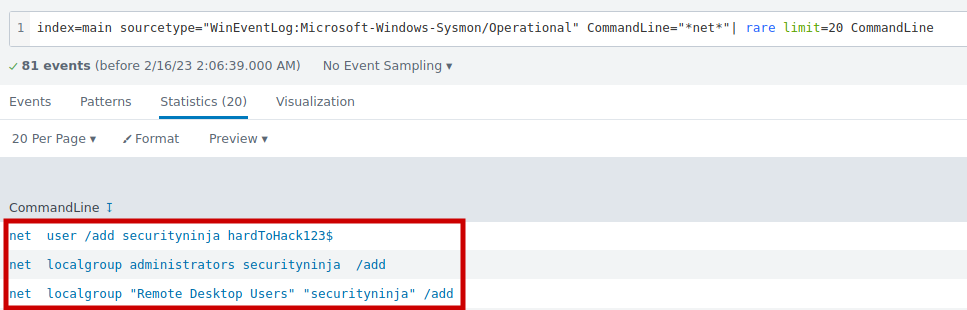
2.5 What was the command the attacker used to add a new user to the compromised system?
We can see that in MITRE Attack framework. Conti uses Command and Scripting Interpreter: Windows Command Shell. net user command is the one that Windows users can use to manage user accounts, read on to know how to add users from CMD.
index=main sourcetype="WinEventLog:Microsoft-Windows-Sysmon/Operational" CommandLine="*net*"| rare limit=20 CommandLine
Answer: net user /add securityninja hardToHack123$
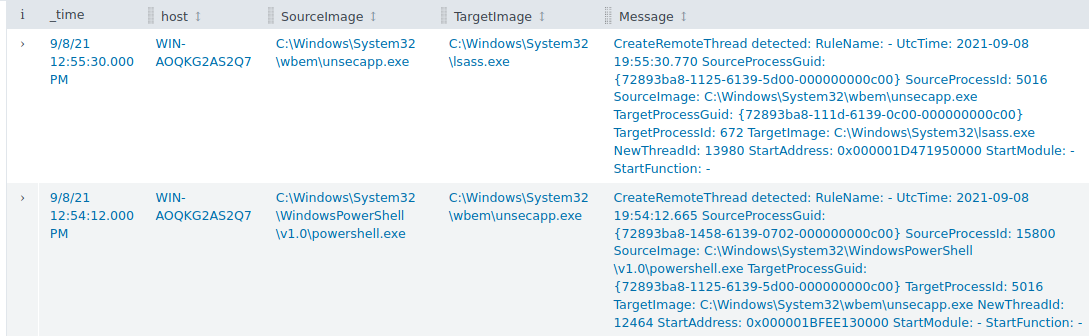
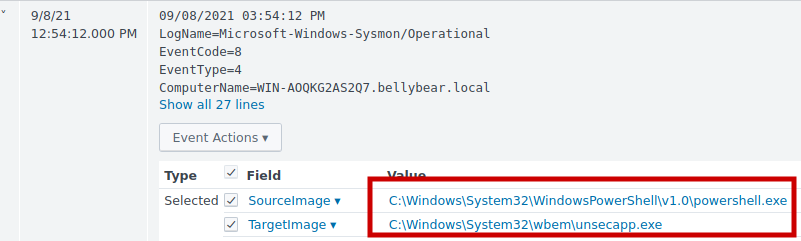
2.6 The attacker migrated the process for better persistence. What is the migrated process image (executable), and what is the original process image (executable) when the attacker got on the system?
CreateRemotethread is a Windows API function that allows a process to create a thread in a different process. This is commonly abused by malware to evade and hide.
index=main sourcetype="WinEventLog:Microsoft-Windows-Sysmon/Operational" EventCode=8
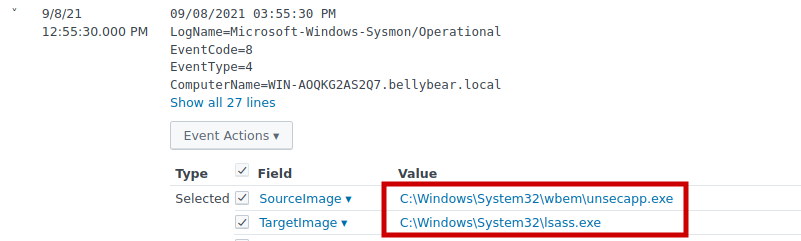
Powershell was used to migrate to unsecapp.exe, and hashes were retrieved using LSASS, which is commonly used by attackers to dump password hashes.
Answer: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe,C:\Windows\System32\wbem\unsecapp.exe
2.7 The attacker also retrieved the system hashes. What is the process image used for getting the system hashes?
Answer: C:\Windows\System32\lsass.exe
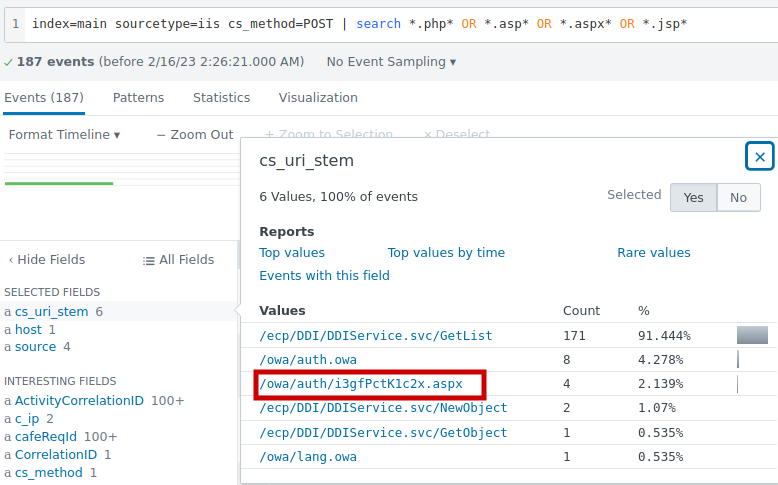
2.8 What is the web shell the exploit deployed to the system?
common webshell collection are PHP ASP ASPX PY JSP JSPX PER. https://www.microsoft.com/en-us/security/blog/2021/02/11/web-shell-attacks-continue-to-rise/
Answer: i3gfPctK1c2x.aspx
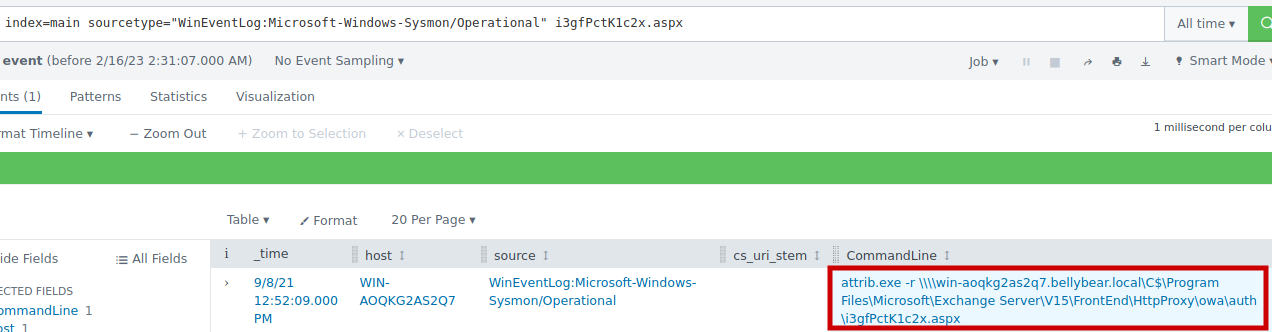
2.9 What is the command line that executed this web shell?
index=main sourcetype="WinEventLog:Microsoft-Windows-Sysmon/Operational" i3gfPctK1c2x.aspx
Answer: attrib.exe -r \\\\win-aoqkg2as2q7.bellybear.local\C$\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\i3gfPctK1c2x.aspx
2.10.0 What three CVEs did this exploit leverage?
Microsoft SMBv3 Remote Code Execution Vulnerability https://nvd.nist.gov/vuln/detail/CVE-2020-0796
Fortinet FortiOS and FortiADC Improper Access Control Vulnerability https://nvd.nist.gov/vuln/detail/CVE-2018-13374
Fortinet FortiOS SSL VPN credential exposure vulnerability https://nvd.nist.gov/vuln/detail/CVE-2018-13379
Answer: CVE-2020-0796,CVE-2018-13374,CVE-2018-13379
References
- https://tryhackme.com/room/contiransomwarehgh
- https://www.bleepingcomputer.com/news/security/fbi-cisa-and-nsa-warn-of-escalating-conti-ransomware-attacks/